[EN] Using MFA for AWS Console and Cli Authentication
Multi-factor Authentication (MFA) is an authentication method that requires the user to provide two or more verification steps. This authentication method requires unique information in addition to regular sign-in credentials. It can be finger prints, one time password from a virtual device or a personal security question. Since these informations are unique for a user and they are less vulnerable to brute force attack, MFA could drastically increase the online security. AWS supports Virtual MFA devices, FIDO security keys and Hardware MFA devices for IAM users and root user. Enabling MFA for AWS is really straightforward.
Enabling MFA for IAM users
- Sign in to the AWS Management Console and open the IAM Users at https://console.aws.amazon.com/iamv2/home#/users
- Open Security credentials tab for the user.
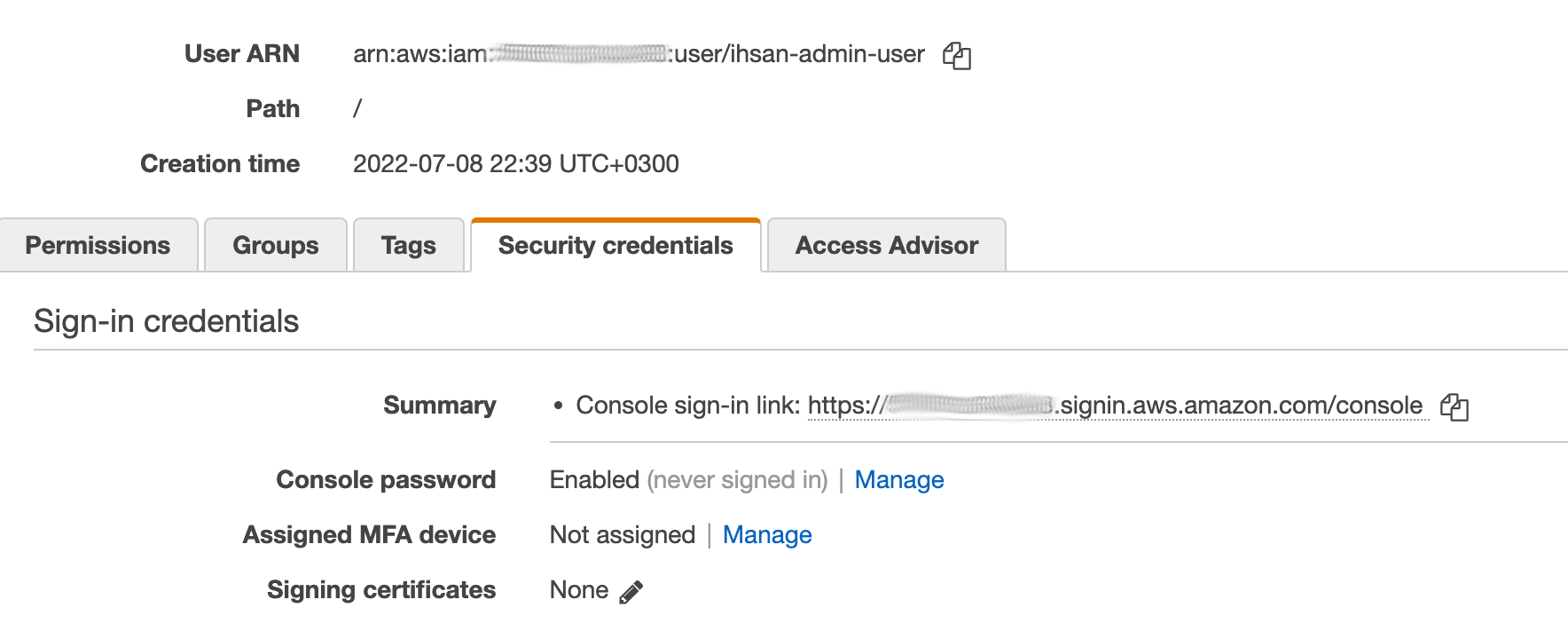
- Click Manage for Assigned MFA device.
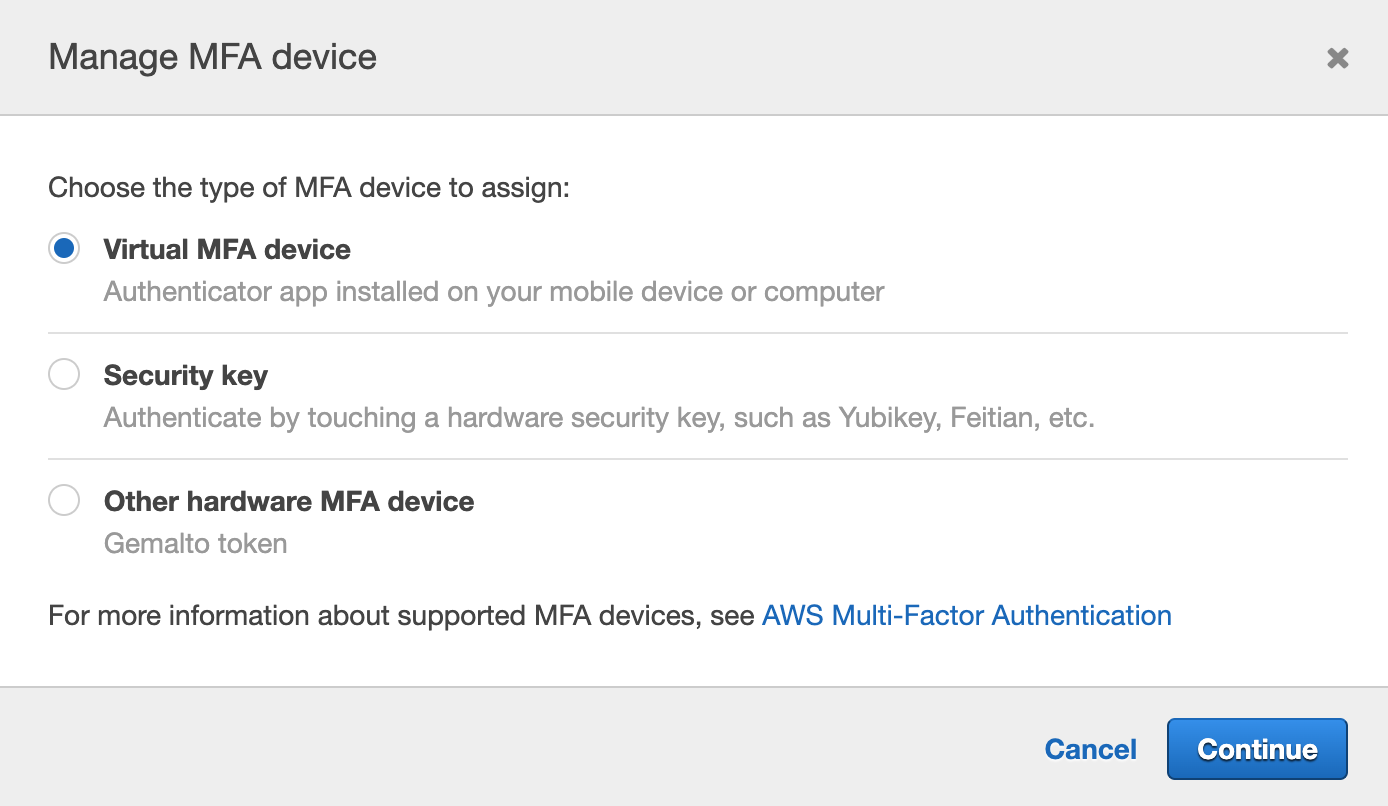
- Select one of the MFA device type.
- Scan QR code and enter MFA code twice.
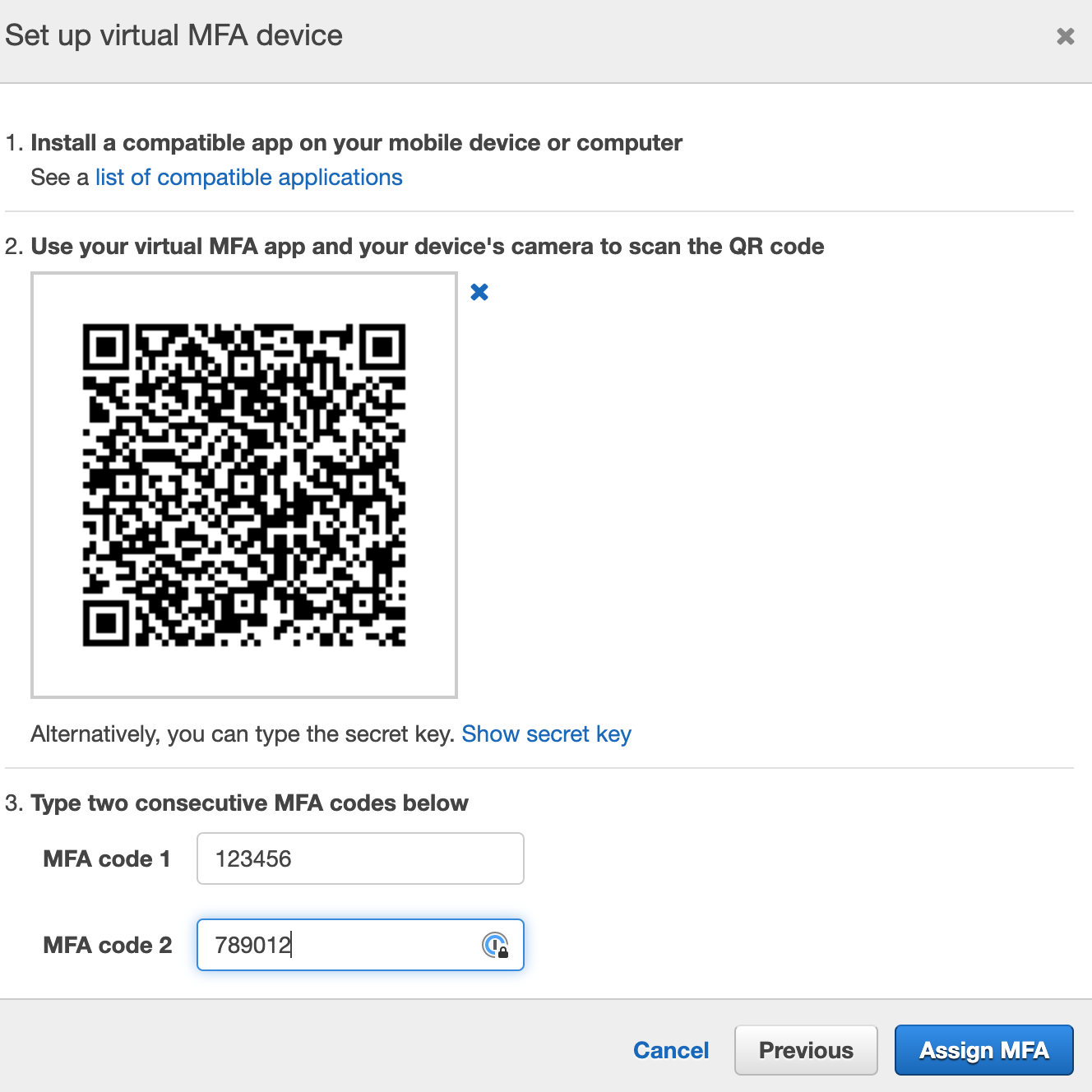
- Complete with clicking to Assign MFA button.
Enabling MFA for root user
- Sign in to the AWS Management Console.
- On the right side of the navigation bar, choose your account name, and choose My Security Credentials.
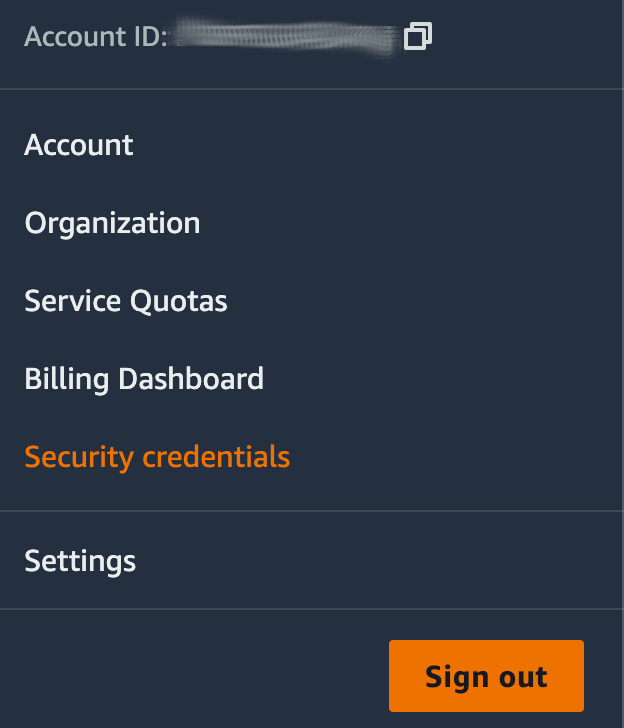
- Expand the Multi-Factor Authentication (MFA) section on the page.
- Choose Activate MFA.
- Select one of the MFA device type.

- Scan QR code and enter MFA code twice.

- Complete with clicking to Assign MFA button.
Using AWS CLI with MFA
Using MFA with AWS CLI is possible with temporary credantials. You need to export temporary credentials to config files or environment veriables then interact with resources.
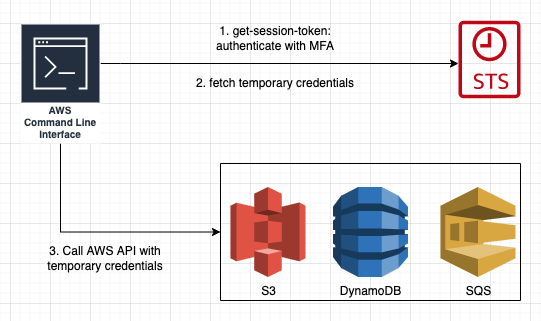
Exporting temporary credentials via cli
- Run the sts
get-session-tokenAWS CLI command
aws sts get-session-token --serial-number arn-of-the-mfa-device --token-code code-from-token
- Output
{
"Credentials": {
"SecretAccessKey": "secret-access-key",
"SessionToken": "temporary-session-token",
"Expiration": "expiration-date-time",
"AccessKeyId": "access-key-id"
}
}
- Export
- Export to environment variables
export AWS_ACCESS_KEY_ID=example-access-key-as-in-previous-output
export AWS_SECRET_ACCESS_KEY=example-secret-access-key-as-in-previous-output
export AWS_SESSION_TOKEN=example-session-token-as-in-previous-output
- Export to ~/.aws/credentials file
[mfa]
aws_access_key_id = example-access-key-as-in-returned-output
aws_secret_access_key = example-secret-access-key-as-in-returned-output
aws_session_token = example-session-Token-as-in-returned-output
Exporting temporary credentials via aws-cli-mfa
aws-cli-mfa is an open-source, command line application for export temproray credentials to ~/.aws/credentials file. I implemented it with golang and it supports multiple platform. You can export temproray credentials and interact aws resources easly.
Configuring aws-cli-mfa
When you enable MFA for an IAM user you can see the MFA serial on console. We need to put that informataion to our aws config file additionally the credentials. Here is the sample configuration:
Installation
You can download the latest prebuild binary from the releases page. Releases
You can clone the go project from the repository and build yourself.
Run these commands to install manually:
export VERSION=1.0.0
export PLATFORM=darwin-amd64
wget https://github.com/icaliskanoglu/aws-cli-mfa/releases/download/$VERSION/aws-cli-mfa-$VERSION-$PLATFORM.tar.gz
tar xzvf aws-cli-mfa-$VERSION-$PLATFORM.tar.gz
sudo mv aws-cli-mfa /usr/local/bin/aws-cli-mfa
~/.aws/config
[my-mfa-profile]
mfa_serial = arn:aws:iam::123454567890:mfa/user-with-mfa
output = json
[profile my-profle]
user_arn = arn:aws:iam::123454567890:user/user-with-mfa
source_profile = my-mfa-profile
~/.aws/credentials
[my-mfa-profile]
aws_access_key_id = ASDDFDSIOFGJPERFOI
aws_secret_access_key = ldfigjpnsvifgjmsdroifgjmdsorifughjbhehe
Run aws-cli-mfa to generate temporary credentials for my-profile with mfa:
We need to get MFA code from the selected device. It will export the temprory credentials to ~/.aws/credentials file.
aws-cli-mfa -p my-profle
Exporting credentials for 'my-profle' profile
Enter MFA Code: 123456
Temporary credentials are exported to '/Users/icaliskanoglu/.aws/credentials'.
After see the success message, you can see the AWS credential in the ~/.aws/credentials file.
...
[my-profle]
aws_access_key_id = example-access-key-as-in-returned-output
aws_secret_access_key = example-secret-access-key-as-in-returned-output
aws_session_token = example-session-Token-as-in-returned-output